There’s an image that’s commonly used to portray cybercriminals.
A hooded character with a Guy Fawkes mask sits behind a laptop and looks out toward the viewer. It’s become the go-to image to accompany any article about bad actors - or even any article about cybercrime in general.
Type the word “hacker” into a Google image search and you’ll see about a hundred different variations of it.
You might think this is just a helpful representation of a mysterious, faceless entity. But actually this generic image speaks to our collective reluctance to understand the hacker.
And this is a problem when we’re living in a world full of sophisticated cyber threats. A world where attacks are arriving from all angles and are becoming more and more brazen.
In such a world, wouldn’t it be better to try to understand who the hacker really is instead of simply assuming that they’re all the same?
Forward-thinking companies are beginning to realize that by doing just that, they can create a much more robust risk analysis.
They’re starting to see empathy for the hacker as a key pillar of a successful cybersecurity strategy.
Just click on this link
In an attempt to summarize the impact of the Covid-19 pandemic, Yuval Noah Harari offered a stark warning. He said that while information technology has made us more resilient against the threat of organic viruses, it has also made us much more vulnerable to the threat of cyber warfare.
When he pondered what the next Covid-19 might look like, the growing number of headlines describing damaging cyber attacks came to his mind.
One of these headlines filled our Twitter feeds recently. It told of the forced shutdown of a vital petroleum pipeline in the US after a ransomware attack. The article warned of the potential impact of such an attack on people’s day-to-day lives. Most notably at the fuel pumps.
As it turns out, it was a pretty astute prediction. Because just a few days later, cybercrime journalist Brian Krebs tweeted the following:
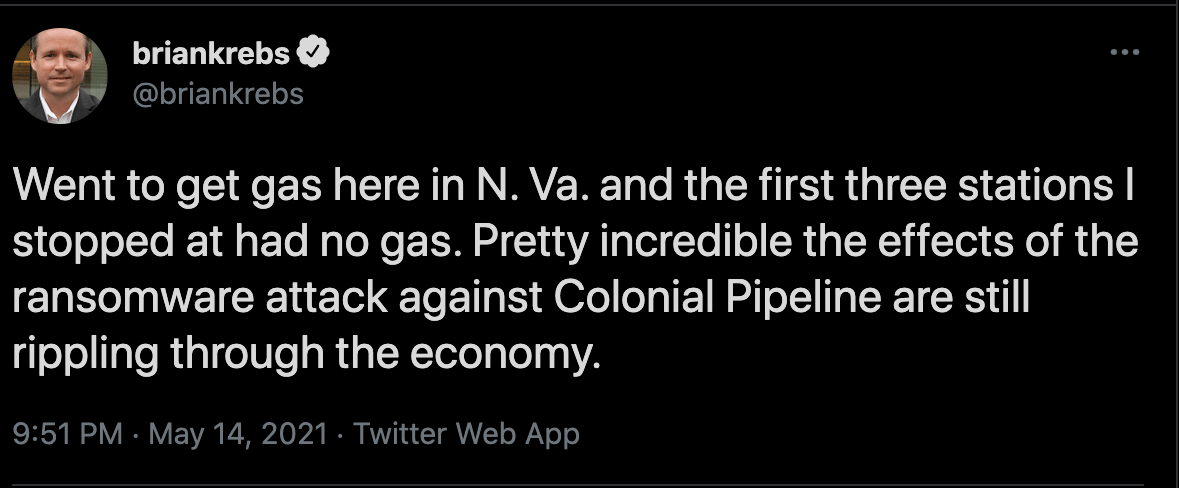
"Incredible" seems like an appropriate word today. But will it continue to be in a few years? Perhaps in the near future inconveniences like this will just be part of our daily lives.
At least that is if the current trends continue in the same direction. With the pandemic as a backdrop, life has been punctuated by phishing emails and texts pinging to our phones. It might have been an issue with your bank account. Or perhaps it was an offer to go and get your first Covid vaccine. Whatever the ruse, the call to action was a grim one laced with malware.
In many ways, a result of all of these attacks has been to bring hackers to the public consciousness more than ever before. But the profile of bad actors is still largely a mystery. It’s the same masked figure staring back at us, offering us nothing.
So, why is it that the default position is still to keep cybercriminals masked and hidden from view?
Who’s really behind the mask?
One answer to the question of why the hacker is deliberately mystified is that investigating who the hacker really is can result in some troubling findings. In many ways it’s far simpler to assume the hacker is some kind of dark, malevolent force who’s interested only in spreading chaos and pain.
The reality, of course, is much more nuanced.
A lot of hackers end up doing what they do almost by accident. Others might be misled or even controlled by those at the head of the criminal gang they work for. Realistically they might have very little option but to continue doing what they’re doing. What’s more, the big picture of how their role is causing damage to lives and livelihoods might be hidden from them.
This isn’t to somehow reduce the significance of the damaging attacks we’ve seen over the course of the last year or so. The intention here isn’t to excuse cybercriminals. After all, hospitals have been attacked, resulting in vulnerable people having vital treatment delayed. Others already impacted by the effects of Covid-19 have had money stolen from their bank accounts.
Instead, what we’re suggesting is that all of us who work in cybersecurity have a responsibility to better understand how somebody becomes a cybercriminal in the first place.
By doing so, we might be able to offer an alternative, more positive path for these people. That should be the end goal.
Until then, the watchword should be empathy rather than ignorance. App developers are quite used to putting themselves in their end user’s shoes, but imagining themselves as a cybercriminal is a much less common exercise.
The first step on this journey is to realize that not all hackers are the same. Some are part of state sponsored groups, while others are individuals who want to test their skills. Most attacks that target businesses come from outside, but some are carried out by employees who feel wronged in some way.
Evolving attacks
Tillie Kottmann, a Swiss hacker who’s part of a group responsible for hacking into the Verkada security camera system, doesn’t fit the typical cybercriminal profile. When asked about the group’s motivations, Kottmann replied:
“Curiosity, fighting for freedom of information and against intellectual property, a huge dose of anti-capitalism, a hint of anarchism — and it’s also just too much fun not to do it.”
Obviously not all cybercriminals are as politically motivated as Tillie. As we’ve said, some have much less agency over their actions. But it’s important to understand that for some groups, motivators aren’t only financial.
For those hackers who are financially motivated - still by far the majority of them - we’ve seen hints in recent months that they’re changing their approach and becoming much more brazen.
A good example of this comes in an article that caught our attention earlier this year. It is about a cyber gang that has taken to reaching out to the customers of their ransomware victims with a view to getting those customers to help with their extortion efforts.
The email the gang would send goes something like this:
“Company X clearly doesn’t care about your data because they haven’t invested in robust cybersecurity. So, do us a favor and tell them how angry you are. And encourage them to pay the ransom we’ve asked for. If you don’t, your personal information might end up on the dark web for a price.”
While cybercriminals attempting to make you complicit in their extortion efforts is a worrying trend, there’s a painful truth here that needs to be acknowledged. In the coming years the effort that a company goes to in order to keep their customer’s data safe will be a key metric.
Alongside the reliability of their product or service and its value for money, a brand will be judged by how seriously they take cybersecurity.
And the modern hacker understands this reality. Like the gang mentioned above, they’ll frame the business that has been lax with its security as the bad guy. The cybercriminal, on the other hand, is simply performing a public duty by highlighting that company’s incompetence.
Keeping on top of evolving trends like this one will be vital to your cybersecurity efforts in the coming years.
Empathy for the hacker
One of the main benefits to app developers of investing time to understand the hacker from the beginning of the development journey is that it results in a much more detailed risk analysis.
Understand the hacker - not only their different profiles, but how their attacks are evolving - and your defensive capability can be vastly improved.
It means you can imagine the parts of your mobile application that might become attack vectors for bad actors further down the line. It makes you think twice about how and where you store your end user’s personal information. And it enables you to empathize even more with that end user by considering how you might educate them about cybersecurity.
For example, by knowing more about the latest phishing trends, you can make it easier for your end users to spot them, too.
Imagine two mobile banks. One of them decides to spend some time in their attacker’s shoes, while the other one thinks it’s a waste of time to think about hackers.
Which of the two would you rather entrust with your priceless personal data and the contents of your bank account?
Empathy for the hacker matters more right now than ever before. Because, as we mentioned earlier, businesses are now judged by how well they protect their end user’s data. We really can’t stress this enough. The modern consumer has so much choice that any kind of security breach simply wouldn't be tolerated by them. They’d take their business to a competitor and their complaints to social media.
The risk for companies is that they lose the trust of their customers before they’ve even had the chance to properly build their reputation.
Fortunately, understanding how threats are evolving doesn’t rely on profiling hackers alone. It can be boosted with threat intelligence.
A lot of businesses are in the dark about the attacks their application is up against in the real world. Threat intelligence is a bit like throwing open the curtains. It allows you to look out at the attacks taking place in your app’s neighborhood.
A threat intelligence system gives you the insights you need to better understand the type of attacks your app might be up against. And this too helps in your risk analysis.
But it also enables you to act on those insights. You can make individual decisions such as blocking access to a user whose activity looks suspicious, for example.
In the financial industry, businesses are already using systems like this to share information about bad actors and paint a more detailed picture of them. It’s an approach that will have to be mirrored in other sectors like healthcare which historically have had more gaps for hackers to exploit.
Really understanding the hacker
When we were deciding on our security by design principles several months ago, we were clear that empathy should play a key role throughout the application development process.
We also knew that what we meant by empathy wasn’t only that designers and developers should understand each other’s challenges. Rather it had to mean everyone on the development team having a keen interest in the potential attacker of the app they were creating.
In a more remote world where mobile apps are becoming key assets in a business' search for success, not to mention being vital to our everyday lives, this has never been more important.
The stakes are simply too high to ignore the hacker or generalize them into a homogeneous entity.
Really understanding the hacker can provide us with two benefits. The first of them is a longer-term aim and infinitely more difficult. That is to better understand what it is about the modern world that is encouraging so many people to become cybercriminals in the first place.
We don’t have the answer to this question yet. But we hope that by continuing to write about this theme and communicating openly with others in the industry, we can get closer to finding one.
The second benefit is much more achievable:
By understanding hackers, you naturally have a better chance of defending against them.
So, it’s time to encourage one another to look under the mask. To find out who that hooded figure really is.
It doesn’t have to be such a mystery anymore.