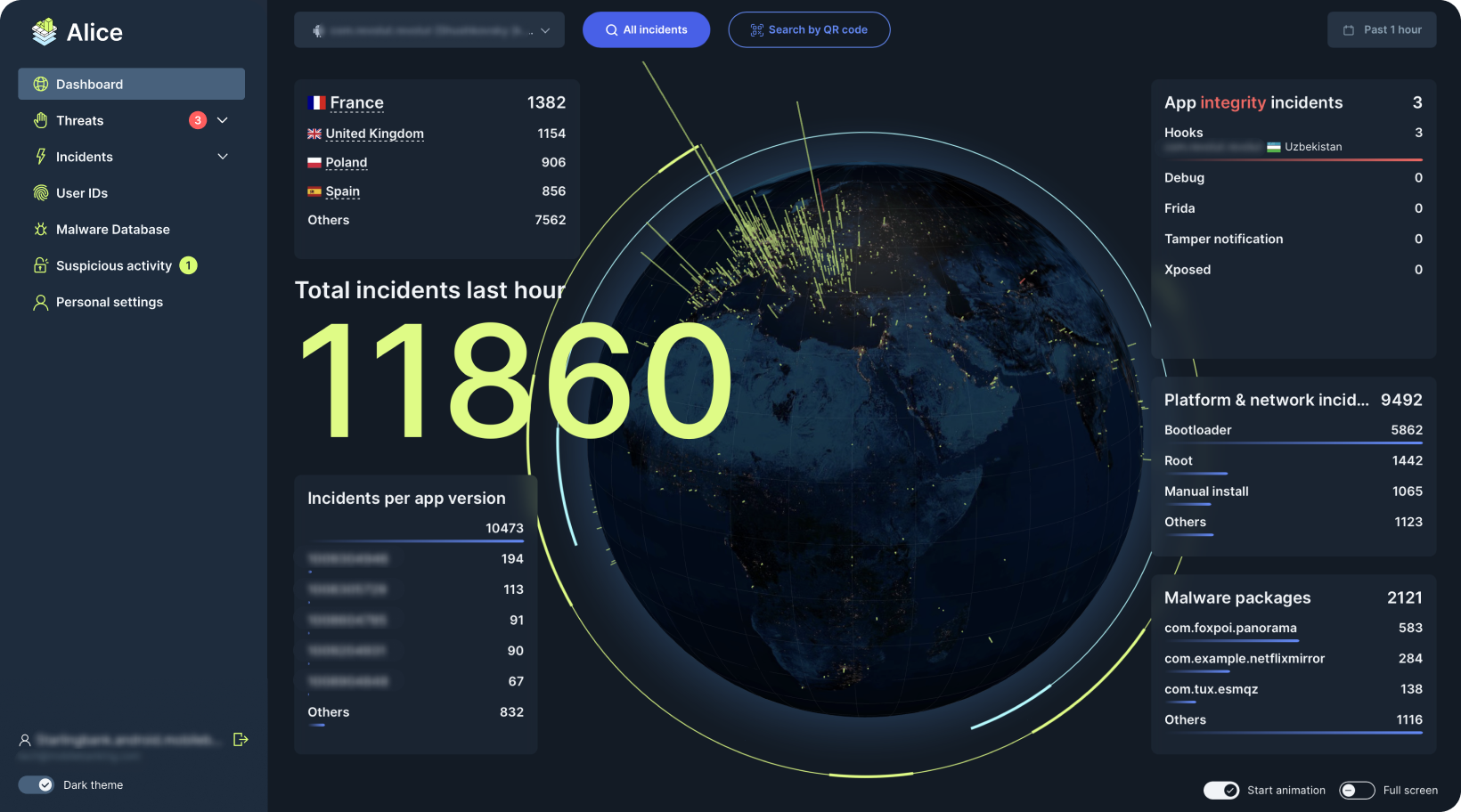
Alice Web Dashboard:
visualize threats and emerging trends, monitor attacks, and get a better understanding of the security posture of your user base
Alice is a mobile app telemetry solution that provides visibility into what is happening on end user devices, enabling you to make smarter security decisions.
Alice ingests signals from trusted in-app sensors - secured by DexProtector - and turns those signals into actionable intelligence for fraud scoring, risk assessment, and analysis by SOC teams.
It therefore provides organizations with greater visibility over their mobile apps, and enables security teams and anti-fraud engines to identify suspicious activity across users, devices, and sessions.
See the unseen: understand the real mobile threat landscape that surrounds your application – from malware to tampering attempts
Act with confidence: use verified, tamper-proof signals to inform fraud scoring, policy enforcement, and customer protection
React in real time: make dynamic, nuanced, and risk-based decisions based on trusted insights
Low friction, high trust: Alice integrates in hours, runs silently, and is built to meet both compliance and sovereignty needs
Yesterday, if you suspected a fraudulent transaction from a mobile app, you might have had no choice but to block the user’s account.
Tomorrow, with Alice, you can make a more nuanced decision. Its trusted signals might tell you that a device’s environment has been compromised, meaning it isn’t appropriate to block the user. Instead, you can choose to delay that one high-value transaction by 12 hours and trigger a step-up authentication.
That way, you stop the potential crime without disrupting the innocent end user.

In the modern world, it’s impossible to trust a signal from a mobile device when you can’t control its integrity. This is a problem because the wrong decisions are being taken on the back of bogus data. There’s simply too much at stake – in terms of money, time, and resources – to continue down that path.
Alice gathers its intelligence from applications protected by DexProtector, which means every signal originates from a trusted, tamper-proof sensor. Attackers can’t spoof, modify, or intercept this data, and so your analysts and SOC team can make important decisions based on real, reliable inputs.
Alice's real-time visibility into the health of your mobile channel and the devices interacting with it is a big help in the fight against mobile fraud.
Identify infected or high risk devices in time to do something about it.

Map trusted signals over time to identify repeat offenders and emerging attack patterns and trends.

Feed Alice data into your fraud scoring system or risk engine for sharper decision-making.

Strengthen your defenses on the back of insights such as the number of untrustworthy devices that are connecting to your app ecosystem.

The mobile app environment is a visibility gap in both Endpoint Detection and Response (EDR) and Extended Detection and Response (XDR).
Alice helps to fill this gap by sharing verified mobile threat intelligence from within the application itself. This matters because the mobile channel is not only the fastest growing endpoint surface, but also the most exposed and vulnerable. Combining Alice’s trusted sensors with the more traditional endpoints and corporate networks covered by EDR and XDR systems can give you holistic visibility of all the cybersecurity challenges you face.
Alice can be easily integrated into SIEM tools, and enables SOC teams to get a view of new threat patterns across the whole mobile channel to facilitate faster, more confident, and more nuanced incident responses.

Speaking of making life easier for your analysts and security teams, Alice offers flexible consumption, with three different ways to use it:
Alice Web Dashboard:
visualize threats and emerging trends, monitor attacks, and get a better understanding of the security posture of your user base

Enterprise API:
easily integrate Alice’s trusted insights into your own internal risk systems, dashboards, or mobile fraud detection and prevention workflows
The Alice Data Stream:
get a real-time feed of global threat data direct from the Licel ecosystem, with intelligence about malware strains, attack types, and device trends


Anti-Malware
Alice draws on its comprehensive malware database to detect and classify thousands of individual strains. This enables your SOC team to know as soon as the malware has been detected and to restrict activity on the device. Real-time, over-the-air updates also mean that you’re protected even against newly discovered threats.


Device Attestation and Intelligence
Alice paints a detailed picture of the devices interacting with your mobile applications, such as the OS version and whether any modifications have been made. Device Attestation checks confirm the integrity and authenticity of the device, while suspicious activity on a device can be tracked over time for enhanced clarity.


User ID Linking
Alice can also use individual user IDs to connect device signals with behavior and session data over a period of time – without revealing Personally Identifiable Information (PII). That way your analysts and SOC team have more substantive and reliable data to work from to make decisions that will affect the access individuals are given.
Alice has no cloud dependencies. It can work fully on-premises if you need it to.
We understand that some organizations demand complete control. If you would rather keep all telemetry and analysis within your infrastructure, that’s fine with us. It’s completely up to you how your data is processed, stored, and shared.
But in a world where mobile malware strains and proxy attacks are evolving on a daily basis, you need a clear direction, visibility, and true signals you can rely on.
Alice doesn’t only make sure that you can see the threats and chart an appropriate course. It also helps you to understand what the signals mean, empowering you to act on them intelligently, securely, and on your own terms.