The mobile malware problem
Mobile malware poses one of the most acute cybersecurity challenges for application developers and owners to solve today.
That’s because malware can result in personally identifiable information, banking credentials, login details, and OTP codes (among other things) being stolen. And the pain that this causes individual users who accidentally download a malicious payload can also cause business headaches further down the line; think reputational damage and regulatory fines.
However, malware is also often seen as something of an invisible threat that is hard to measure, quantify, and visualize.
Our threat intelligence solution, Alice, is helping to change that.
Alice helps our clients to understand the threats that float and flutter around their application so that they can plot a sound security strategy more easily. Its data (based on attacks that our mobile channel protection solution, DexProtector, is preventing) tells a coherent story about where threats are coming from and how they are evolving.
We’ll tell you one of these stories in the following paragraphs. For this particular one, we wanted Alice to focus on the Indian market; a dynamic landscape full of innovative mobile applications and, sadly, bad actors unleashing sophisticated threats.
Detecting the netflixmirror malware
We’ve been enhancing and updating both Alice and DexProtector consistently over the past couple of years with a view to identifying specific forms of malware more effectively. This commitment to continuous improvement is illustrated neatly in the chart below which shows the number of malware detections by DexProtector’s Build ID, with the latest build at the top.
We’re committed to developing our detection capabilities in the months and years ahead in order to continue to spot and stop malicious malware variants as they emerge and before they can cause any lasting damage.

While Alice was able to detect lots of different forms of malware spreading in India during our sample time period of August 2024, one of them clearly stood out as the most dangerous and prolific.

The malware com.example.netflixmirror was detected on user devices more than 629,000 times.
The name itself is interesting as it reflects a pretty common trend with malicious malware variants; they will often be named in such a way that they don’t stand out as looking suspicious. Netflix is one of the most popular streaming services out there, while screen mirroring solutions are incredibly common, too.
Hijacking authentic technologies and digital platforms can give malware a false level of legitimacy and help it to slip under the radar.
The graph below shows us that the number of daily unique installs of apps affected by the netflixmirror malware in India grew rapidly throughout our sample month of August 2024.

But how exactly does a malware variant like this spread?
The infection takes root
Alice’s data can also be used to paint a picture of the correlation between incident count and first occurrence count per package. The graph below suggests that as the number of malware incident detections increases, so too do the number of first occurrences – there is clearly a proportional, linear relationship.

This might lead us to the conclusion that malware packages (including the netflixmirror variant) behave similarly in terms of how they spread. The data also hints at detection methods consistently identifying new infections – or first occurrences – at a similar rate across different malware packages and similar rates of both spread and detection, regardless of their total incident count.
But let’s come back to the netflixmirror malware.
The graphs above are useful for providing us with the context of malware detection, but we wanted to explore – and visualize – exactly how this malware was able to spread so rapidly across an entire country.
The video below gives you an idea of how the malware spawned in Mumbai, spreading to other locations in Maharashtra. Then it really snowballed, gaining traction in the fast-growing tech cities of Bengaluru and, especially, Hyderabad. At the end of our selected time period, the malware has extended its reach to almost every corner of the country and has taken root up north in the capital, New Delhi.
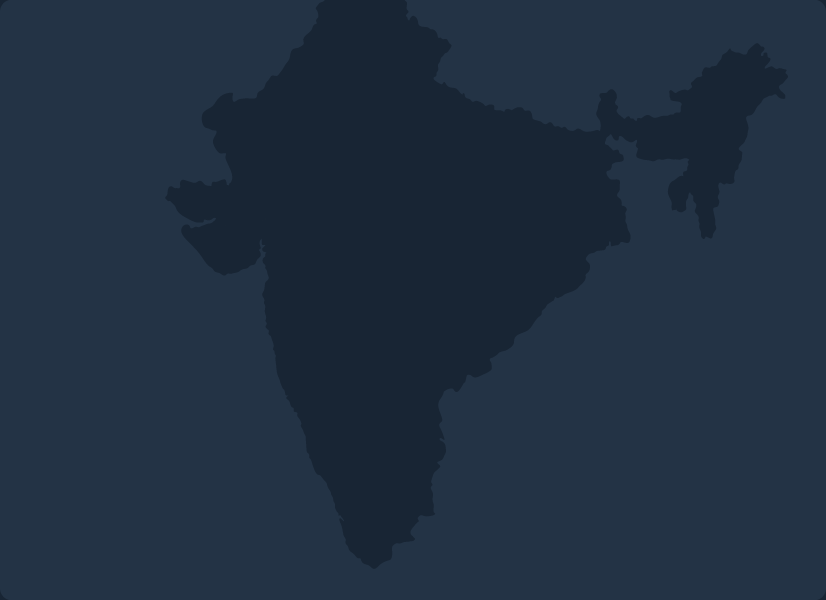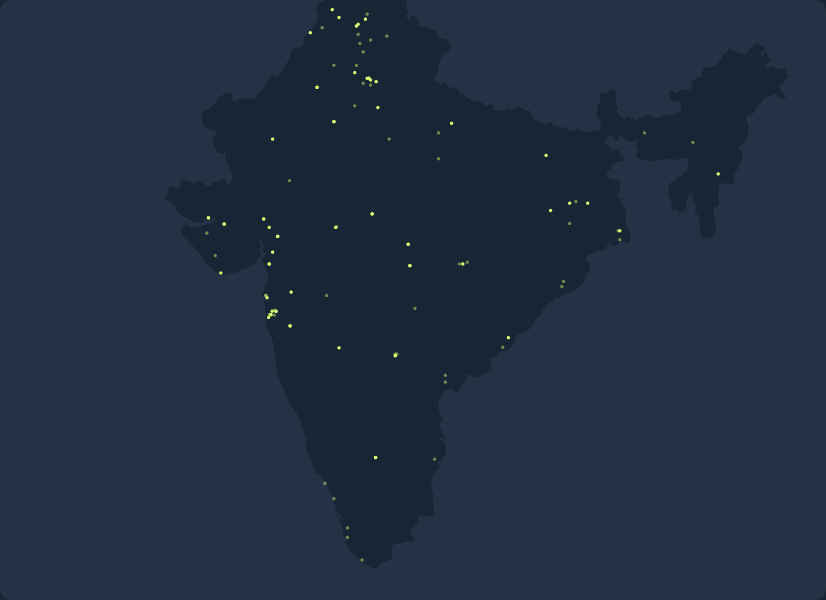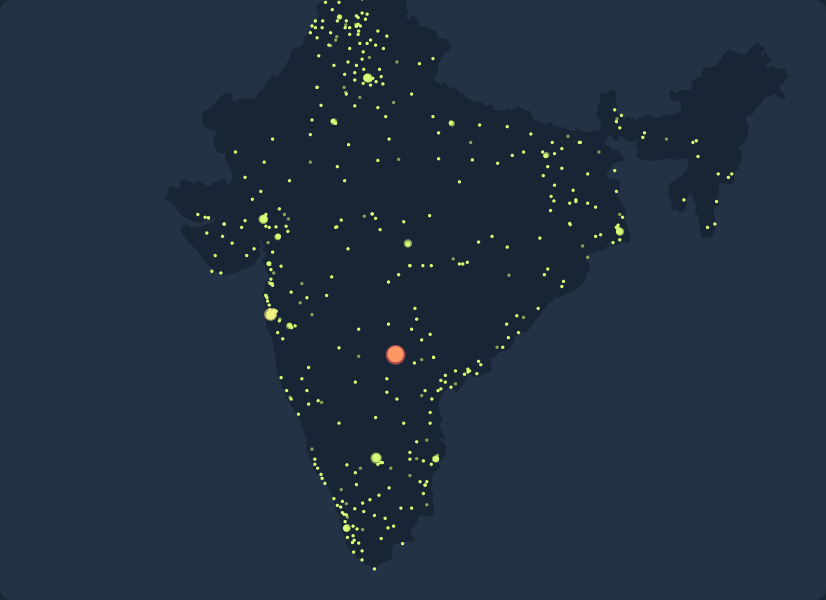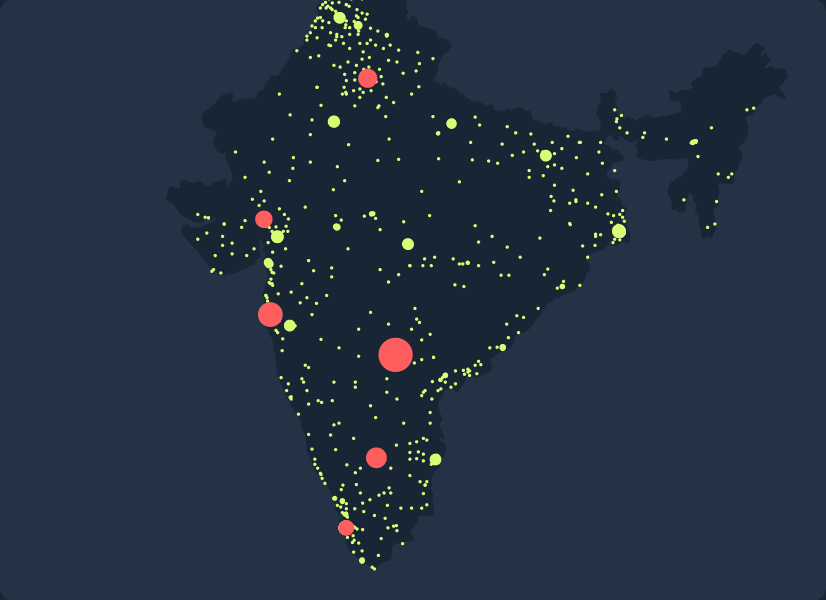
How malware spreads
Social engineering is undoubtedly a big factor in the speed with which the netflixmirror malware was able to spread across India. As we said earlier, this malware was clearly named with a view to tricking people into thinking they were downloading something legitimate and authentic – at least for those who were aware they had downloaded it.
Imagine receiving an email, text, or message from a messaging app when you’re busy and on the move that references Netflix or screen sharing. Perhaps the messaging is framed around an update that enhances your viewing experience. It’s easy to imagine clicking on a link and ending up downloading a bogus, malware-laden app by mistake.
App users can also be directed to third-party app stores and pushed to download cloned versions of legitimate apps. They can be encouraged to forward on bogus promotions related to the app harboring the malware via messaging apps. And malware can also land on victims’ devices via compromised adverts and malicious QR codes.
All of these scenarios help to explain how dangerous malware variants can spread so quickly around a country with a huge population of young, digitally-savvy people.
Mitigation measures
Detecting malware is only half of the battle, of course.
Here at Licel, our Anti-Malware module leverages both Alice Threat Intelligence and DexProtector. That means our clients’ applications are integrated with malware and Potentially Harmful App (PHA) detection capabilities. This can be customized according to individual requirements and delivers instant “over-the-air” updates.
More directly, our UI Protection module can mitigate the most common techniques malware uses to steal sensitive personal information. For example, it prevents some of the go-to Accessibility Services exploits on Android such as screenshots, screen sharing, and screen recording.
In the case of this netflixmirror package, our solutions enabled our clients to prevent their apps from functioning on devices infected with the malware.
Mobile malware is a particular problem in the mobile banking industry. Read our use case to find out how we’re solving security challenges in this key sector.




