This month marks twelve years since the first commercial licence for DexProtector. While a lot has changed in the mobile threat landscape since then, our mission hasn’t.
In this edition of the Layers Bulletin, we’re sharing how the latest updates to DexProtector and Alice continue to advance mobile channel security. We’ll also look to the future and share our vision for secure Digital ID solutions.


What's new with Licel's solutions?
DexProtector
DexProtector delivers advanced mobile application protection by enforcing runtime integrity, verifying device trust states, and leveraging adaptive threat intelligence to identify evolving attack vectors. The latest update expands its scope even further.
Fraudsters who exploit rooted devices and modified firmware are continuously updating their toolset. In recent weeks, we've seen an increase in use of modules (such as TrickyStore) aiming to defy hardware attestation, one of the most robust methods to detect potentially untrustworthy devices. That's why the latest version of DexProtector introduces enhanced mechanisms to ensure stricter hardware attestation, building on threat and device intelligence gathered and maintained by the Licel security research team.
Screen capture and screen sharing can leak the most sensitive user data, fuelling the activities of malware and fraudsters. Many apps have existing preventions, but most do not reflect the latest threats. These include screen capture tools which exploit shell-level privileges to create virtual displays which are wrongly flagged as secure, especially on older versions of Android. The latest version of DexProtector adds new UI Protection capabilities which specifically mitigate such virtual display tools (e.g. scrcpy, Vysor), as well as overlay injection attacks, and also enable configurable responses.
One of our main aims is for DexProtector to combine the simplest configuration with the most robust security. This aim was what led us to introduce new Automatic Protection capabilities, starting with Automatic Protection for Manifest Classes, which is available in the latest version. This option ensures that all classes declared in the Android Manifest - entry points to the application which form part of its potential attack surface - are automatically targeted by DexProtector for key code protection mechanisms.
Last but not least: DexProtector's Mobile API Protection capability is now available for iOS, in addition to Android, delivering unified, policy-driven API integrity and attestation across platforms. For more details on why this expansion so important, keep reading below.
Alice Threat Intelligence
Alice Threat Intelligence is a key component for mitigating modern attacks against mobile applications and user data. The latest version introduces a redesigned Dashboard UI that provides real-time visualizations of prevented attacks and correlated threat activity across devices.
A new Alice Incidents Data Feed enables seamless integration with enterprise SIEM/SOAR platforms through a dedicated, real-time data streaming interface. This feed supports environments with high incident volumes and real-time event analysis, allowing Security Operations teams to correlate mobile threat data with broader organizational telemetry.
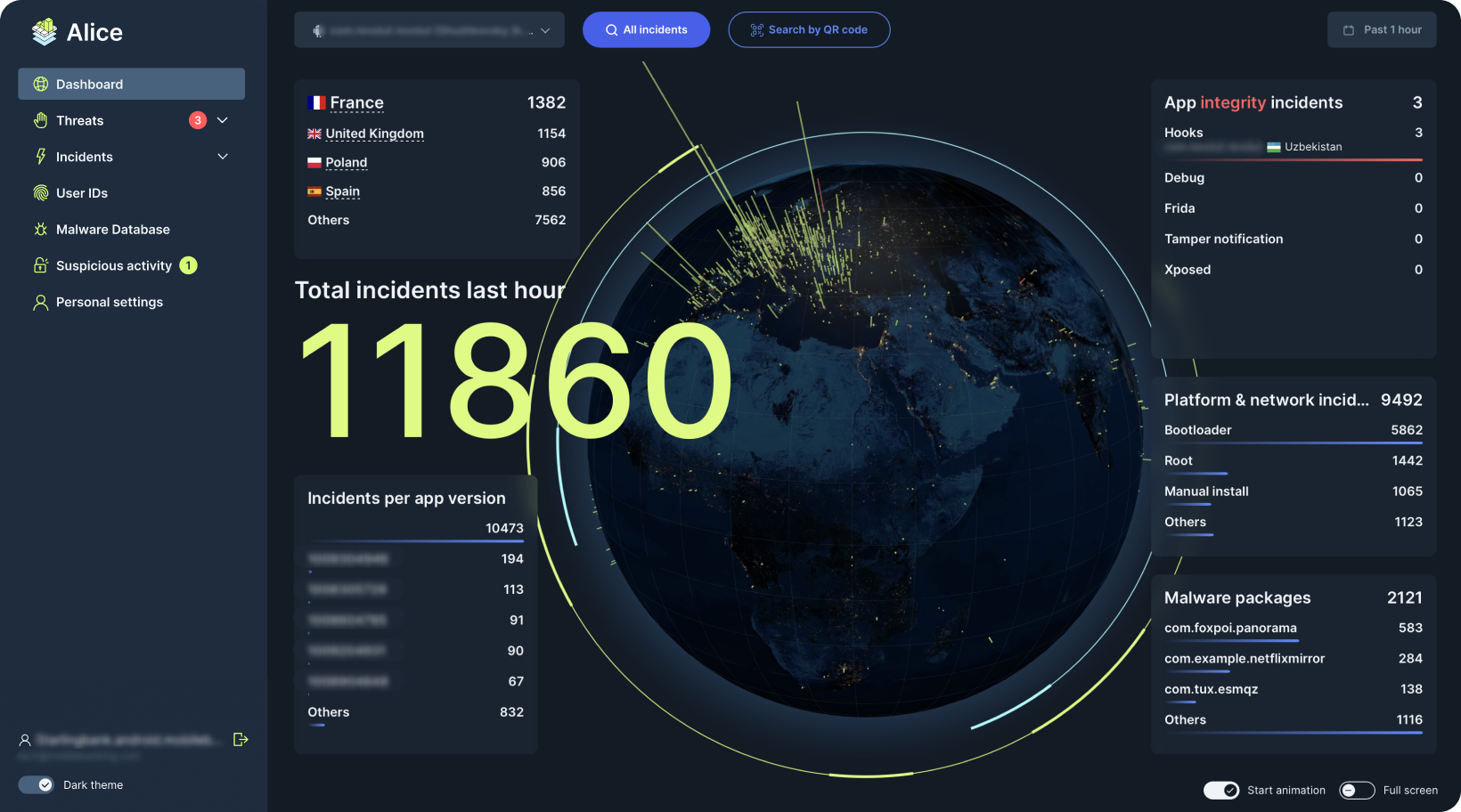


Attack trends
The growing need for Mobile API Protection on iOS
In recent months, we’ve seen a significant uptake in the deployment of our DexProtector Mobile API Protection mechanism to mitigate critical security and business threats, including botnets, bonus program abuse, and fraudulent communication with hardware NFC digital wallets.
While these deployments have been successful, the underlying threat vector - unsecured APIs - is not confined to a single operating system. Threats evolving and multiplying, particularly on iOS, meant that a more holistic security response was required. So, as we mentioned earlier, we have extended DexProtector's Mobile API Protection capability to iOS.
Apple's introduction of app side-loading capabilities in the EU earlier this year has resulted in the iOS platform becoming an increasingly attractive target for attackers. It’s a shift that fundamentally alters the threat model for iOS, introducing risks such as app tampering and cloning that were previously associated primarily with more open ecosystems like Android.
Client requests have always been a big product development and improvement driver for us, and it was clear there was a growing demand among our customer base to extend Mobile API Protection to iOS. It ensures seamless security across both platforms, extending DexProtector’s integrity-first architecture to safeguard the communication channel between mobile applications and their backends. DexProtector’s Mobile API Protection technology enables client backend servers to check the JWT token; if the verification of that token fails, that means it is not the original, authentic app but rather a tampered version of it, a clone, or a bot, for example. As such, DexProtector helps to makes sure that only authentic and integrity-verified app instances can access protected APIs.
Our guiding principles for secure Digital Identity
As governments and organizations worldwide race to roll out digital identity programs, the conversation is increasingly shifting from “when” to “how”. Digital ID comes with huge promise, such as seamless access to services and borderless verification. But as identity moves to the smartphone, the attack surface also changes dramatically. The same convenience that allows users to authenticate in seconds can also allow malware to compromise an entire system in a matter of moments. That’s why we believe that true Digital ID Protection starts with making sure that every mobile interaction, operation, and transaction happens within a secure, tamper-proof environment.
At Licel, we’re speaking with task forces, integrators, and wallet developers about how to implement secure digital identity solutions that citizen end users can genuinely trust. We provide layered, certifiable protection across the mobile channel, from code hardening and runtime integrity control to cryptographically secure operations and real-time threat and device intelligence. This holistic protection is vital if Digital ID solutions are to go beyond compliance alone and deliver lasting confidence, privacy, and resilience.
Licel achieves the respected CSA Cyber Trust Mark
Licel has achieved the highest level (Advocate) of the Cyber Security Agency (CSA) of Singapore’s Cyber Trust Mark Certificate in recognition of the design, development, delivery, and maintenance of DexProtector, the Licel vTEE, and Alice Threat Intelligence.
Alongside the ongoing EMVCo evaluation and approval for DexProtector and the Licel vTEE, and our ISO/IEC 27001:2022 compliance, this certification acts as validation for our consistent security-first philosophy.


Meet us in London and Bangkok
The Licel team are sponsoring two exciting events in the next week. We’d love to see you there if you’re planning to attend.
From the 30th - 31st October, we’ll be at Droidcon London. This is the third consecutive year that we’ve been gold sponsors of the event, which is highly significant for us because Droidcon has always meant a lot. Over a decade ago now we gave a talk at Droidcon Berlin that helped to reinforce our belief in the need for robust mobile channel protection to help developers to deliver secure apps that would build long-term trust. This year we’ll be talking about how to make sure you don’t lose your identity in 2035.
Then, from the 5th-6th November, we’ll be sponsors of the PCI SSC Asia Pacific Community Forum in Bangkok; it’s an event that brings together leaders who are helping to shape global payment security standards. As mobile payments continue to evolve, Licel’s mission is to help ensure they remain secure - and so sponsoring this forum reflects our long-term commitment to building trust and resilience in the mobile payments channel.


Droidcon London // PCI SSC Asia Pacific Community Forum Bangkok.
Droidcon 2025 and PCI event
Thanks for reading this edition of the new and improved Licel Layers Bulletin. We'll be back next month with more product improvement updates and threat intelligence insights.





