iOS
Alice - Threat Reporting and Telemetry
Using Alice with DexProtector
Once your app has been released, DexProtector continues to monitor its security as it is being used anywhere in the world, with all data about risks, threats, and attacks being sent automatically to your account in Licel’s Attack Telemetry and Threat Intelligence Service (Alice).
Alice offers an easy-to-use dashboard where you can keep track of key incidents as they occur, including any cases of HTTP public key pinning anomalies, tampering, and crashes. You can view these incidents according to when and where they took place, and you can tailor the output data to suit your reporting needs.
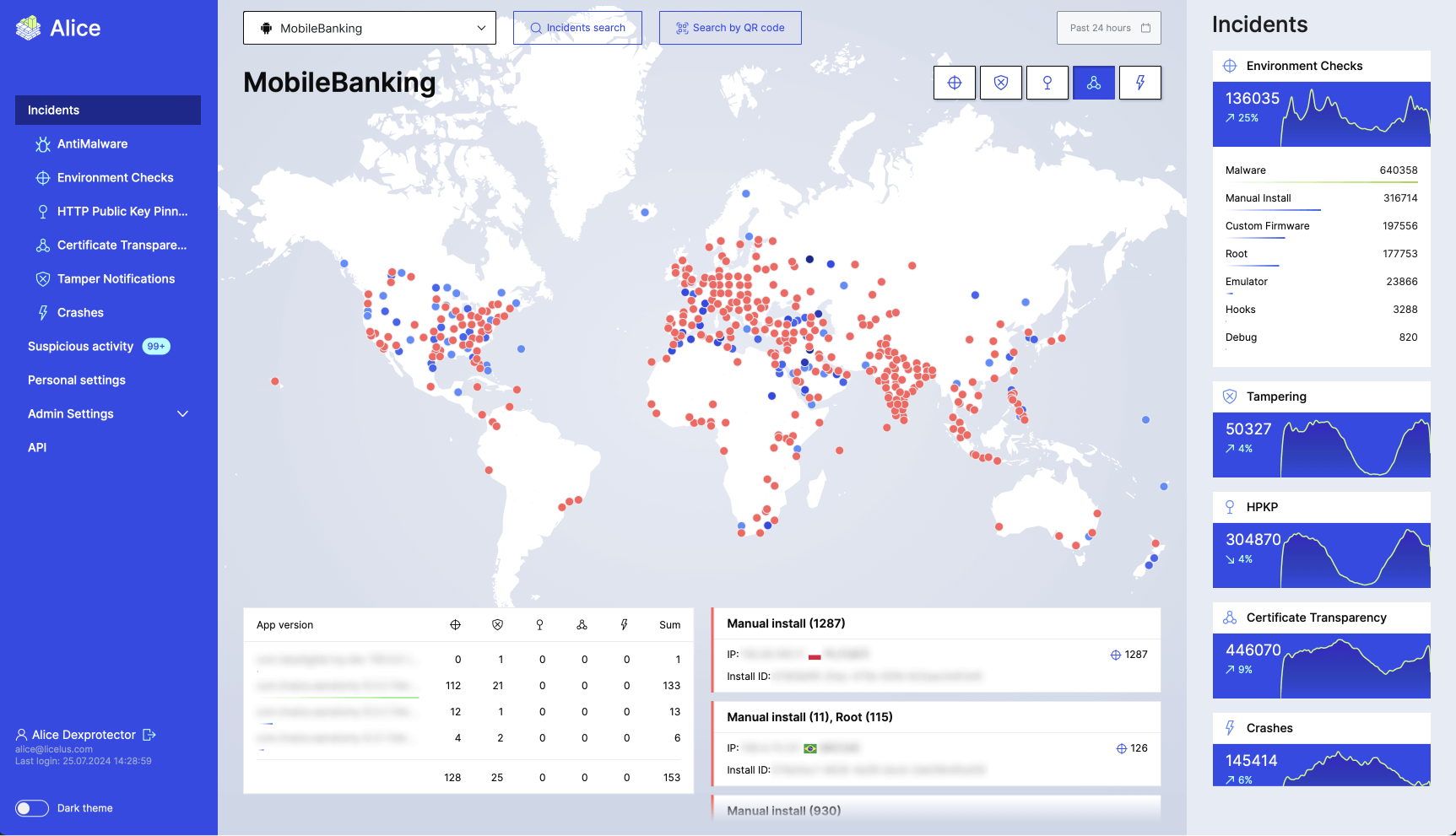
DexProtector and Alice can also work in combination with your own risk analysis system, so that you have the security monitoring information you need in the form that works best for your organization.
The result is that you have an easy-to-use overview of every incident, from the moment it happens; a flexible search tool which sorts by attack type and content; and notifications every time DexProtector’s defences are triggered.
Getting started with Alice
1. Get login credentials for Alice
If you are already have an active DexProtector Enterprise license, simply fill out this form with a request for sign-in details to Alice, or contact us at primary@licelus.com.
2. Copy the API key for Alice integration
Log in to alice.licelus.com with the username and password you have received. On the Alice start page, you will find a unique automatically generated key that you can use to integrate Alice when configuring DexProtector.
3. Enter the API key in the DexProtector configuration file
Use DexProtector Studio or edit the configuration file directly by adding the <reportMonitoring> element and <apiKey> nested element, as follows:
'
<reportMonitoring>
<apiKey>137feb09-f390-4f00-b43f-ebccf530adf6lt</apiKey>
</reportMonitoring>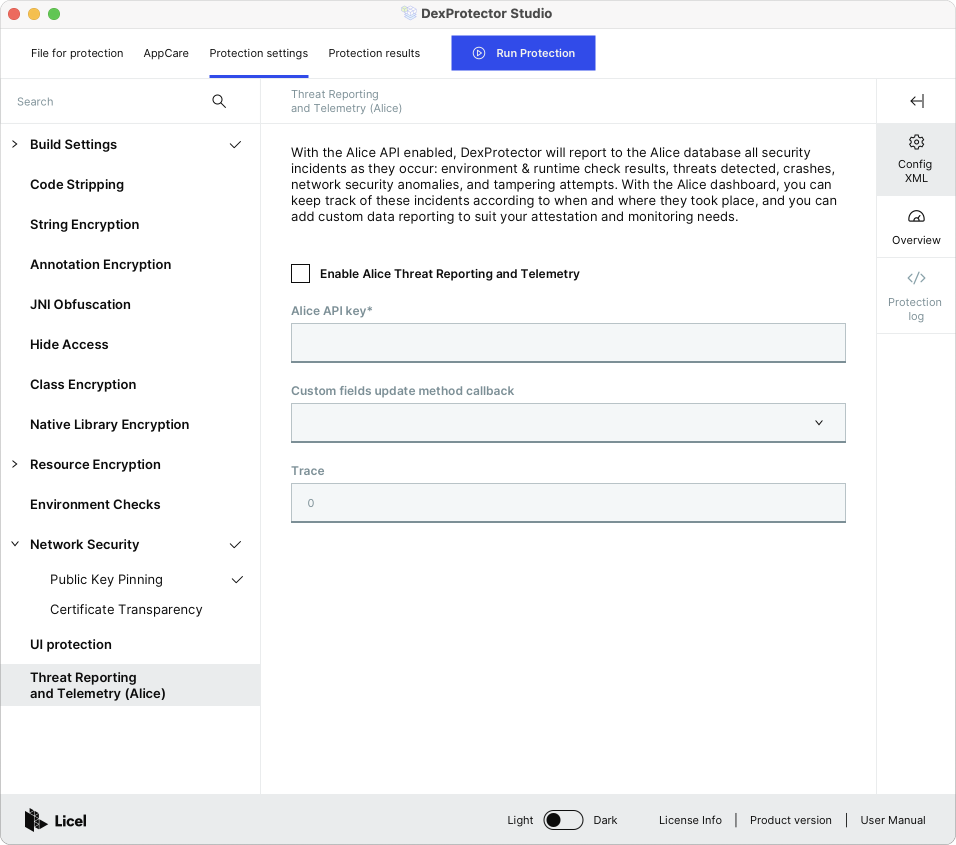
4. Protect the application and get the first reports
Protect your application using the modified configuration file. Your Alice API key will be integrated into the application during DexProtection. Then, when the application detects a threat, a report will be signed in to Alice using this key. If your key is compromised for any reason, you can generate a new key in Alice and block the old one. You will be able to generate an incident yourself or wait for real incidents. While there are no incidents, Alice displays only the start page and a demo project. As soon as new incidents occur, your application will report to Alice automatically.
-
What is DexProtector?
Introduction to DexProtector > What is DexProtector? -
Obfuscation & Encryption Capabilities
Introduction to DexProtector > Obfuscation & Encryption Capabilities -
RASP, Security, and Anti-Fraud Capabilities
Introduction to DexProtector > RASP, Security, and Anti-Fraud Capabilities -
Overview
DexProtector for iOS > Overview -
1. Download
Getting started > 1. Download -
2. Activate
Getting started > 2. Activate -
Activate via CLI (online)
Getting started > Activate via CLI (online) -
Activate via CLI (offline)
Getting started > Activate via CLI (offline) -
Activate via DexProtector Studio (online)
Getting started > Activate via DexProtector Studio (online) -
Activate via DexProtector Studio (offline)
Getting started > Activate via DexProtector Studio (offline) -
3. After activation
Getting started > 3. After activation -
Introduction to configuring DexProtector
Configuring DexProtector > Introduction to configuring DexProtector -
Configuration file overview
Configuring DexProtector > Configuration file overview -
Filters: A guide to targeting resources
Configuring DexProtector > Filters: A guide to targeting resources -
Resource Encryption
Configuring DexProtector > Resource Encryption -
Configuring DexProtector for applications
Configuring DexProtector > Configuring DexProtector for applications -
JavaScript and HTML-based Hybrid and Cross-Platform Apps
DexProtecting Hybrid and Cross-Platform Applications > JavaScript and HTML-based Hybrid and Cross-Platform Apps -
Flutter
DexProtecting Hybrid and Cross-Platform Applications > Flutter -
Frameworks
DexProtecting iOS Frameworks and XCFrameworks > Frameworks -
XCFrameworks
DexProtecting iOS Frameworks and XCFrameworks > XCFrameworks -
Overview
DexProtector Studio > Overview -
Using DexProtector Studio: DexProtector JAR and License File
DexProtector Studio > Using DexProtector Studio: DexProtector JAR and License File -
Managing DexProtector JAR and License File
DexProtector Studio > Managing DexProtector JAR and License File -
Activating your license via Studio (online)
DexProtector Studio > Activating your license via Studio (online) -
Activating your license via Studio (offline)
DexProtector Studio > Activating your license via Studio (offline) -
Protecting your iOS app or Framework with DexProtector Studio
DexProtector Studio > Protecting your iOS app or Framework with DexProtector Studio -
Protection Recommendations
DexProtector Studio > Protection Recommendations -
Load Package for Protection
DexProtector Studio > Load Package for Protection -
Manage Protection Settings
DexProtector Studio > Manage Protection Settings -
Run Protection and View Protection Results
DexProtector Studio > Run Protection and View Protection Results -
Final Checklist
Completing the DexProtector Process > Final Checklist -
Run DexProtector via the CLI
Completing the DexProtector Process > Run DexProtector via the CLI -
Run DexProtector via DexProtector Studio
Completing the DexProtector Process > Run DexProtector via DexProtector Studio -
Using Alice with DexProtector
Alice - Threat Reporting and Telemetry > Using Alice with DexProtector -
General FAQs - DexProtector for iOS
FAQs > General FAQs - DexProtector for iOS -
FAQs on Installation, Activation, Configuration, and Distribution
FAQs > FAQs on Installation, Activation, Configuration, and Distribution
Link copied!